This blog covers what phishing is, why its is so effective, the stages of a phishing attack, how users can identify an attack and how to protect your businesses data from these attempts.
Phishing summarised in 60 seconds
Phishing is one of the most effective techniques used by hackers today to illegally obtain sensitive information from individuals and businesses. Phishing earnt its name due to the methods resemblance to that of fishing. A hacker essentially throws multiple “lines” out in an attempt to catch unsuspecting victims with their “bait”. However, the “line”, in this case, is either a phone call, email or social post and the bait is a believable situation that would require a recipient to share sensitive information. The process relies heavily on the hacker’s ability to manipulate the receiver via a flawlessly crafted and believable message that doesn’t beg any questions.
How serious is phishing?
In 2018, Phishlabs research noted a 40.9% increase in phishing attacks. Further research by the Department for Digital, Culture, Media & Sport found that 43% of UK businesses experienced a data breach, 66% of which were deceived by a successful phishing attempt. While phishing attempts spare no man, attackers particularly target businesses and organisations carrying high volumes of sensitive data. Some of the main industries targeted include finance, education, government and military, healthcare and retail. Depending on the level of sophistication and degree of the attack the impact on businesses can be critical to their survival. While there may have been an immediate loss of data and money, the long-term effects are a loss of trust and reputational damage.

Why is phishing so popular?
With a society constantly primed and ready, thanks to our undeniable reliance on the internet for day-to-day activities, hackers are never short of opportunity. Furthermore, the low cost, high reward nature of the technique teamed with its extensive success rate means- attackers will not be retiring the technique anytime soon. To avoid falling prey to this relentless attack on our security, we must educate ourselves and our workplaces.
The stages of a phishing attack
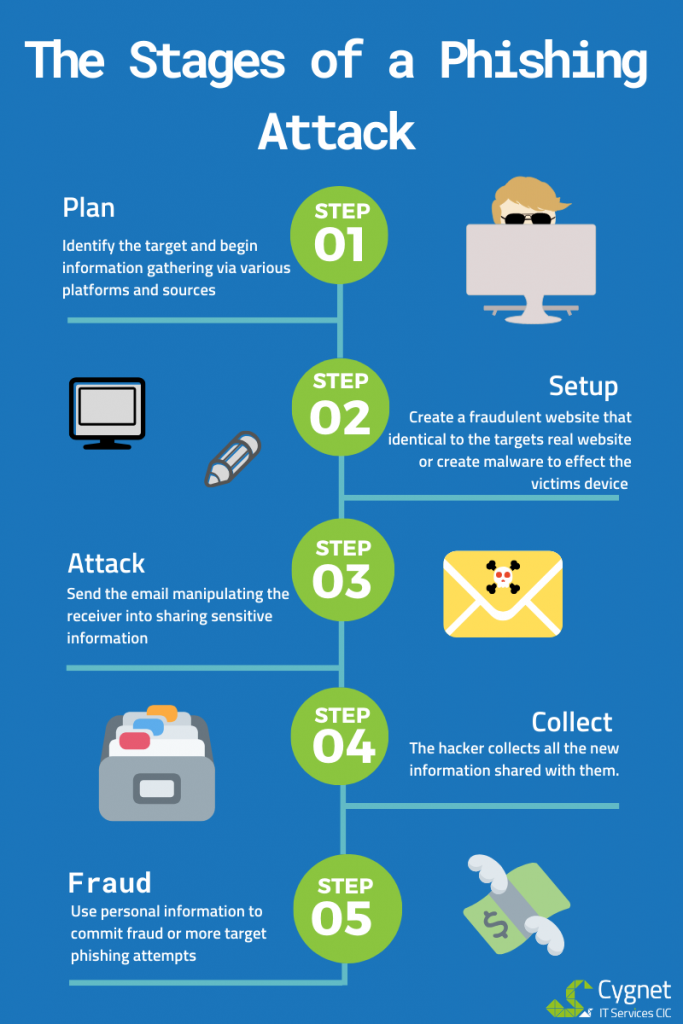
The stages of a phishing attack are best summarised by Natasha M. Wojcicki in her breakdown of the 5 stages of a phishing attack, illustrated by the infographic above.
Stage 1- Plan: Identify the Target (individual or an organisation) and begin gathering relevant information from websites, calling, visiting the premises, or monitoring network traffic.
Stage 2- Setup: Create a fraudulent website that is identical to
the targets real website or create malware that will execute on the recipient’s
device (mobile or computer). This malware may capture keystrokes or lock down
the receiver’s computer files and ask for ransom.
Stage 3- Attack: The attacker will send the email to their target disguised as a trustworthy or reliable source such as a bank, service provider, friend, colleague etc. The email will usually be concerning an issue that requires urgent action, leading the recipient to update information, click a link, reset a password or provide other sensitive information without question.
Stage 4- Collect: The information shared by the recipient is then collected from whichever medium they utilised (email, website, or keystrokes).
Stage 5- Fraud: Now the Phisher has the recipient’s personal information (credit card number, website credentials, bank account details) they can commit illegal transactions, identity theft and other various forms of fraud.
How do I identify a phishing email?
You may be wondering at this point if there is any software available to identify if an email is safe or a phishing attempt. The answer is yes. There are email filtering and anti-phishing tools available, however, they are only successful in stopping 35% of phishing attempts. Essentially, these tools try to identify threatening emails by scanning for terminology commonly used by phishers. Unfortunately, much of that terminology is also used in everyday business email-hence the success of email phishing. While these tools assist in providing some protection, the real line of defence comes from staff being able to identify and outsmart the phisher. Here are some ways you can identify a phishing email.
Public Email Address
The email has been sent from a public email instead of a company email domain (e.g. Joeblogs@cygnet.it). If you’re unsure, always click to see the full email just in case. Sometimes, hackers will attempt to hide a public email address by:
1.Changing the domain name to a company name. By doing this, the receiver of the email will potentially only see the business name when the email appears in their inbox (e.g. you have received an email from Cygnet) leading them to think it’s a safe email to action.
2.Changing the local part of the address to a business name (e.g. Cygnet@gmail.com)
Poorly Written Email
The email is poorly written containing grammatical errors, incorrect spelling, missing words or lacking clarity. This may be the case for one of two reasons
1. It’s a technique to identify targets who may be gullible, aren’t paying close attention to their emails/online interaction or lack awareness of phishing. Often managed manually, this provides hackers with ideal targets who are unlikely to recognise what has happened before it’s too late.
2. Hackers are often from non-English speaking countries and so their emails may come through filled with grammatical errors. While attackers will generally put their emails through a spell checker, grammatical errors or missing words may go unnoticed.
There is a Sense of Urgency
Often, these emails will come with a sense of urgency tied to them. The hacker’s goal is to make the receiver react without thinking and share whatever information it is they have requested.
There is an action required
Emails will usually contain a request to click a link, visit a website, transfer funds, require you to log in to an account or ask you to directly share sensitive information. They may also contain an attachment, such as an invoice, which they will request you open and check. Before reacting to any of these you should first check if they are what they perceive themselves to be!
You will know if an attachment is infected if: there is a pop-up warning about the file’s legitimacy, the application asks you to adjust your settings or you are contacted regarding an invoice you were not expecting.
A suspicious Link can be identified by checking the destination address before clicking the link. This is simple to do, even if the email only provides a button you can hover over the button with your mouse and the address will appear. On your phone, hold your finger on the button and a pop-out address will appear. If the address does not match the businesses official websites address do not click the link.
Is Phishing a Long or Short Term Concern?
The sad reality is, phishing is not something that will be disappearing anytime soon. The process is highly lucrative for hackers and few offenders are apprehended due to jurisdiction issues. Therefore, hackers continue to evolve their techniques, finding opportunities within new technology, leveraging popular social platforms and exploiting human behaviour. The best defence for businesses is to educate staff on what phishing is, the alternative methods used and how to identify it in action.
As a rule, if you receive an email that seems suspicious and shows any of the signs of phishing mentioned in this blog, approach with caution. The safest way to get confirmation an email is legitimate is to contact the sender directly via an alternative channel. Additionally, if you experience any phishing attempts we encourage you to report these attempts to the police via Action Fraud.
How else can we protect our data from these attacks?
While there is no software capable of stopping all phishing attacks, there are some designed to protect against malware and viruses and ensure the business continues operating if there is a data breach.
Anti-malware and anti-virus provide a constant line of defence, fighting any encrypted emails that may attempt to infect your device. Both work hand-in-hand to fight known viruses, new emerging threats, ransomware and trojans that your business may become exposed to. Another form of protection is backup and disaster recovery. If businesses experience a breach, the interruption to its operations can be critical. Ensuring you have some type of disaster recovery and data backup in place will ensure this does not happen. Often businesses think their cloud platforms are already backed up by the provider, but this is not necessarily the case. Always ensure you have your own in-house or professionally outsourced backup and disaster recovery in place for optimum protection.
Until substantial defence software has been created, we suggest staying on top of any phishing news updates and ensure your staff are as well. To simplify this process, we will regularly post updates about any phishing or hacker related news via our Facebook and Twitter.




